- PRODUCTS
- COMPANY
- SUPPORT
- PRODUCTS
- BY TYPE
- BY MARKET
- COMPANY
- SUPPORT
Bringing Payments to the Cloud with FIPS Certified LiquidSecurity®2 HSMs
Payment-specific Hardware Security Modules (HSMs)—dedicated server appliances for performing the security functions for credit card transactions and the like—have been around for decades and not much has changed with regards to form factor, custom APIs, “old-school” physical user interfaces via Key Loading Devices (KLDs) and smart cards. Payment-specific HSMs represent 40% of the overall HSM TAM (Total Available Market), according to ABI Research1.
The first HSM was built for the financial market back in the early 1970s. However, since then HSMs have become the de facto standard for more General-Purpose (GP) use cases like database encryption and PKI. This growth has made HSM usage for GP applications 60% of the overall HSM TAM. Unlike Payment HSMs, where most deployments are 1U server form factors, GP HSMs have migrated to 1U, PCIe card, USB, and now semiconductor chip form factors, to meet much broader use cases.
The typical HSM vendors that offer both Payment and GP HSMs have opted to split their fleet. They deploy Payment specific HSMs that are PCI PTS HSM certified for payments and GP HSMs that are NIST FIPS 140-2/3 certified. If you are a financial institution that’s government mandated to deploy a fleet of Payment HSMs for processing payment transactions, but also have a database with Personally Identifiable Information (PII) data that needs to be encrypted to meet General Data Protection Regulation (GDPR) or California Consumer Privacy Act (CCPA), you would also need to deploy a separate fleet of GP HSMs. This would include two separate HW, two separate SW, and two operational teams to manage each. Accordingly, the associated CapEx/OpEx spending is significant.
For Cloud Service Providers (CSPs), the hurdle was insurmountable and forced many to deploy dedicated bare metal 1U servers to offer payment services in the cloud. These same restrictions that were forced on financial institutions were now making their way to CSPs. Also, this deployment model is contrary to why CSPs have succeeded in the past, which was to offer when they offered competitively priced services as needed on shared resources.
A fundamental shift away from “old school” to “new school” is occurring with the Marvell® LiquidSecurity family.
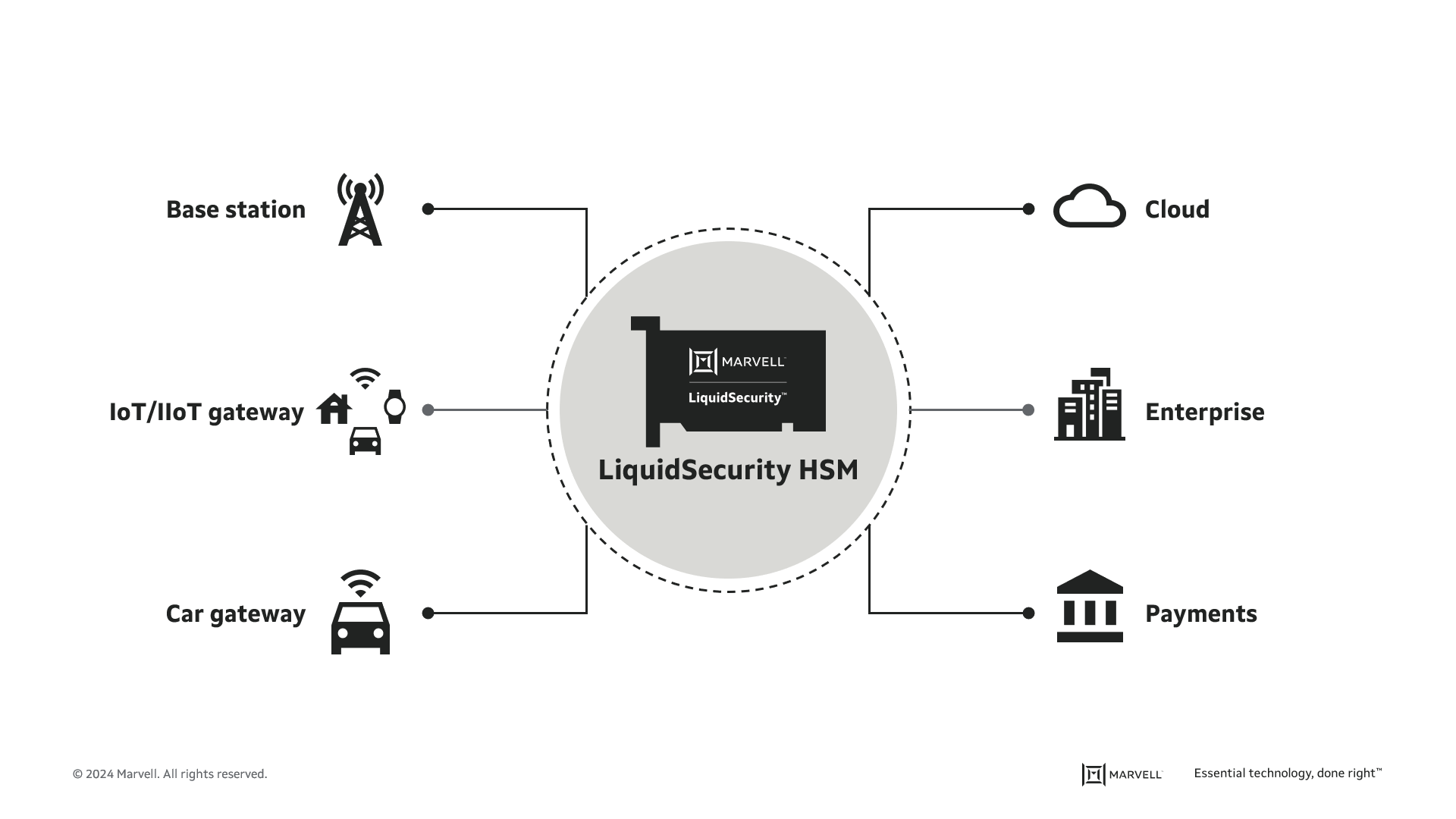
The LiquidSecurity family is driving the shift from having HSMs on premise to in the cloud. Instead of having to buy their own, banks can subscribe to HSM services from the cloud, making it easier to be secure. Also, by using a chip card instead of a whole server, costs are decreased for cloud service providers because less power and space are used.
Announced last year, LiquidSecurity2 (LS2) increased the number of keys stored on a single device to 1 million (a 10x improvement), the number of simultaneous ECC transactions to 120,000 and the number of partitions per card to 42. Six out of the ten largest cloud service providers have integrated the LiquidSecurity platform into their operations in a variety of ways.
But for payments, PCI PTS HSM certification is needed.
Now, the Marvell LS2 has achieved both NIST FIPS 140-3 Level-32 and PCI PTS HSM3 certifications on the same hardware and firmware. A first in the industry, CSPs are no longer relegated to offering separate hardware for both services.
Marvell has led the effort to transform HSMs into cloud-based services since the release of our first LiquidSecurity HSM back in 2015, and we continue collaborating to innovate more solutions and influence the workflows of our customers. Uniting HSMs onto the cloud is a step towards more accessible and sustainable security.
1 ABI Research
2 CMVP NIST FIPS 140-3, Level-3 Certification
# # #
Marvell and the M logo are trademarks of Marvell or its affiliates. Please visit www.marvell.com for a complete list of Marvell trademarks.
This blog contains forward-looking statements within the meaning of the federal securities laws that involve risks and uncertainties. Forward-looking statements include, without limitation, any statement that may predict, forecast, indicate or imply future events, results or achievements. Actual events, results or achievements may differ materially from those contemplated in this blog. Forward-looking statements are only predictions and are subject to risks, uncertainties and assumptions that are difficult to predict, including those described in the “Risk Factors” section of our Annual Reports on Form 10-K, Quarterly Reports on Form 10-Q and other documents filed by us from time to time with the SEC. Forward-looking statements speak only as of the date they are made. Readers are cautioned not to put undue reliance on forward-looking statements, and no person assumes any obligation to update or revise any such forward-looking statements, whether as a result of new information, future events or otherwise.
Tags: Security
Recent Posts
- Marvell Wins LEAP Award for 1.6T LPO Optical Chipset
- Co-packaged Optics: Powering the Next Wave of AI Data Center Innovation
- AI Scale Up Goes for Distance with 9-meter 800G AEC from Infraeo and Marvell
- Faster, Farther and Going Optical: How PCIe Is Accelerating the AI Revolution
- Marvell Wins Leading EDGE Award for Ara 1.6T Optical DSP
Archives
Categories
- 5G (10)
- AI (42)
- Cloud (17)
- Coherent DSP (11)
- Company News (102)
- Custom Silicon Solutions (8)
- Data Center (65)
- Data Processing Units (21)
- Enterprise (24)
- ESG (10)
- Ethernet Adapters and Controllers (11)
- Ethernet PHYs (3)
- Ethernet Switching (41)
- Fibre Channel (10)
- Marvell Government Solutions (2)
- Networking (42)
- Optical Modules (18)
- Security (6)
- Server Connectivity (32)
- SSD Controllers (5)
- Storage (22)
- Storage Accelerators (2)
- What Makes Marvell (45)
Copyright © 2026 Marvell, All rights reserved.
- Terms of Use
- Privacy Policy
- Contact

