- PRODUCTS
- COMPANY
- SUPPORT
- PRODUCTS
- BY TYPE
- BY MARKET
- COMPANY
Our Company
Media
Contact
- SUPPORT
The Race Against Automotive Hackers Is Accelerating
“In your garage or driveway sits a machine with more lines of code than a modern passenger jet. Today’s cars and trucks, with an internet link, can report the weather, pay for gas, find a parking spot, route around traffic jams and tune in to radio stations from around the world. Soon they’ll speak to one another, alert you to sales as you pass your favorite stores, and one day they’ll even drive themselves.
While consumers may love the features, hackers may love them even more.”
The New York Times, March 18, 2021
Hacking used to be an arcane worry, the concern of a few technical specialists. But with recent cyberattacks on pipelines, hospitals and retail systems, digital attacks have suddenly been thrust into public consciousness, leading many to wonder: are cars at risk, too?
Not if Marvell can help it. As a leading supplier of automotive silicon, the company has been intensely focused on identifying and securing potential vulnerabilities before they can remotely compromise a vehicle, its driver or passengers.
Unfortunately, hacking cars isn’t just theoretical – in 2015, researchers on a laptop commandeered a Jeep Cherokee 10 miles away, shutting off power, blasting the radio, turning on the AC and making the windshield wipers go berserk. And today, seven years later, millions more cars – including most new vehicles – are connected to the cloud.
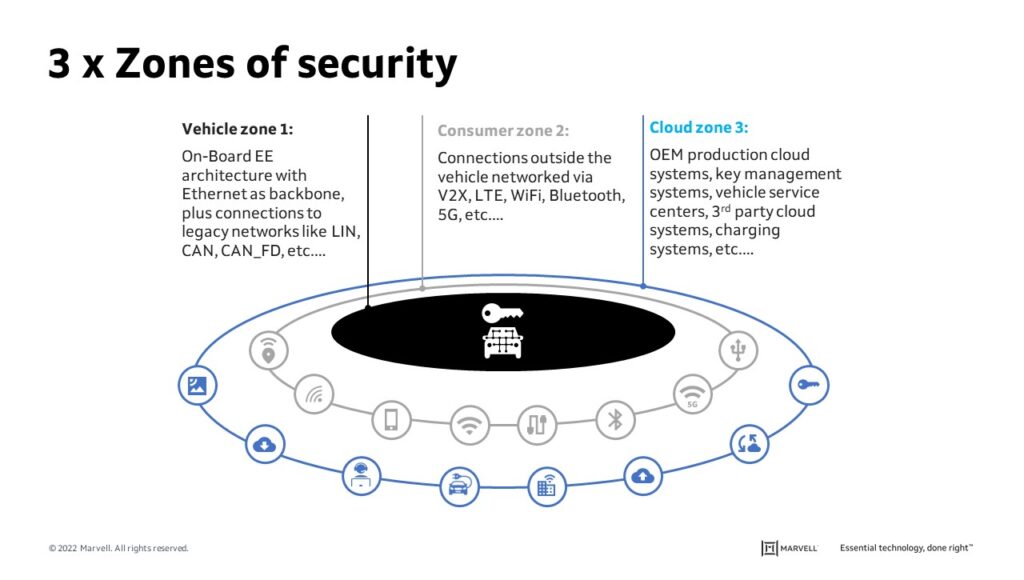
As such, these cars operate within a larger digital ecosystem. Elements include not just entertainment, navigation, and a wide array of third-party apps, but ultrasonics, RADAR, LIDAR, camera and other data generated by a growing number of automotive sensors and those of nearby vehicles. In most cases, such data is extremely time-sensitive; no driver can afford to wait even a second to know if the warnings or images they see on their screen are accurate and trustworthy.
This exacting standard of trust and reliability means that every source of data or data exchange must be secured against delay or interference of any kind, whether that exchange is vehicle-to-vehicle, vehicle-to-infrastructure, vehicle-to-network or vehicle-to-people. Put simply, the data has to be 100% spoof-proof.
To ensure this, automotive engineers are incorporating an array of new security features – many of which have already been proven in other industrial applications – into the design of a vehicle’s original E/E Architecture: the electronics hardware, network communications, software and wiring that together enable the vehicle’s digital operations and interactions.
There are multiple common use-cases that require robust, proactive protection at the silicon and software level in order to protect the vehicle, its drivers and passengers:
- When vehicle manufacturers update software/firmware or allow third parties to do so, they must ensure that upgrades can only be completed under secure conditions and protocols. This can be achieved with a secure Boot, implemented within the silicon’s firmware.
- When vehicles receive time-sensitive data from external sources to update maps, infrastructure, traffic, and infotainment, that data must be secure and verifiably accurate.
- When a vehicle’s sensor technology, such as RADAR, LIDAR or cameras, scan surroundings for potential hazards, the data they generate must be secure and verifiably accurate.
- When vehicles communicate with each other about their relative position, speed and direction of travel, that data must also be secure and verifiably accurate.
To ensure such security, accuracy and reliability, every layer in the data exchange mechanism must be protected through robust protocols, encryption and authentication. Obviously, these challenges are complex, and do not lend themselves to a one-size-fits-all solution. Rather, they require multiple security mechanisms within the silicon (including those from Marvell), along with well-designed interfaces that facilitate the development and use of corresponding, secure firmware and software.
One such security mechanism under consideration in the next generation of Automotive EE Architectures is Media Access Control Security (MACsec). MACsec thwarts hackers by authenticating and encrypting data as it travels between a sensor and its destination. MACsec fortifies in-vehicle networking by securing data exchanges on a point-to-point and hop-by-hop basis, preventing Layer 2 security threats such as intrusion, man-in-the-middle, and replay attacks.
Notably, just as ISO 26262 is now a mandatory design specification for vehicle safety systems, ISO/SAE 21434 and UNECE Regulation 155 will also become critical as vehicles become part of a larger, connected digital ecosystem. These standards will create a common language for communicating and managing cybersecurity risk in designing and producing road vehicles and their E/E systems, including their components and interfaces. Such unified standards will become increasingly critical to protecting the integrity of the entire road-based transportation system, especially as vehicles and hackers both become more sophisticated.
As the Automotive Information Sharing and Analysis Center (AUTO-ISAC) has stated, “an attack on one is an attack on all.” Given this shared vulnerability – and mutual interest in thwarting cyberattacks – collaboration between OEMs, Tier 1, Tier 2 and Tier 3 supply-chain providers is going to be essential in the years ahead, and Marvell is proud to be a partner in this collaborative ecosystem.
For several years now, drivers have come to expect vehicular safety features that previous generations would never have imagined possible. From blind-spot warnings to automatic vehicle spacing to airbags that only deploy in the worst of crashes, we live in a world of rising standards and expectations. Now, automotive data security is steadily climbing the public’s list of priorities, too. Because in the race against hackers, the slow lane is not an option, and there is no finish line.
Tags: Automotive EE Architectures, Automotive Hackers, E E Architecture, ISO 26262, ISO SAE 21434, MACsec, UNECE Regulation 155
Recent Posts
Archives
Categories
- 5G (12)
- AI (26)
- Automotive (26)
- Cloud (14)
- Coherent DSP (8)
- Company News (101)
- Custom Silicon Solutions (6)
- Data Center (48)
- Data Processing Units (22)
- Enterprise (25)
- ESG (6)
- Ethernet Adapters and Controllers (12)
- Ethernet PHYs (4)
- Ethernet Switching (39)
- Fibre Channel (10)
- Marvell Government Solutions (2)
- Networking (34)
- Optical Modules (13)
- Security (6)
- Server Connectivity (25)
- SSD Controllers (6)
- Storage (22)
- Storage Accelerators (2)
- What Makes Marvell (38)
Copyright © 2024 Marvell, All rights reserved.
- Terms of Use
- Privacy Policy
- Contact